CTF 竞赛模式简介¶
解题模式 - Jeopardy¶
解题模式(Jeopardy)常见于线上选拔比赛。在解题模式 CTF 赛制中,参赛队伍可以通过互联网或者现场网络参与,参数队伍通过与在线环境交互或文件离线分析,解决网络安全技术挑战获取相应分值,类似于 ACM 编程竞赛、信息学奥林匹克赛,根据总分和时间来进行排名。
不同的是这个解题模式一般会设置 一血 、 二血 、 三血 ,也即最先完成的前三支队伍会获得额外分值,所以这不仅是对首先解出题目的队伍的分值鼓励,也是一种团队能力的间接体现。
当然还有一种流行的计分规则是设置每道题目的初始分数后,根据该题的成功解答队伍数,来逐渐降低该题的分值,也就是说如果解答这道题的人数越多,那么这道题的分值就越低。最后会下降到一个保底分值后便不再下降。
题目类型主要包含 Web 网络攻防 、 RE 逆向工程 、 Pwn 二进制漏洞利用 、 Crypto 密码攻击 、 Mobile 移动安全 以及 Misc 安全杂项 这六个类别。
战争分享模式 - Belluminar¶
在 2016 年世界黑客大师挑战赛(WCTF)国内首次引入韩国 POC SECURITY 团队开创的 BELLUMINAR CTF (战争与分享)赛制,从此中国国内陆陆续续也有开始 BELLUMINAR 模式的比赛,目前采取这一赛制的有 2016 年诸葛建伟老师集合的 XMan 夏令营分享赛以及同年 9 月的「百度杯」CTF 比赛。
同时这里也有 BELLUMINAR 赛制的介绍官网: http://belluminar.org/
赛制介绍¶
Belluminar, hacking contest of POC, started at POC2015 in KOREA for the first time. Belluminar is from 'Bellum'(war in Latin) and 'seminar'. It is not a just hacking contest but a kind of festival consisted of CTF & seminar for the solution about challenges. Only invited teams can join Belluminar. Each team can show its ability to attack what other teams want to protect and can defend what others want to attack.
如官网介绍这样,BELLUMINAR CTF 赛制由受邀参赛队伍相互出题挑战,并在比赛结束后分享赛题的出题思路,学习过程以及解题思路等。战队评分依据出题得分,解题得分和分享得分,进行综合评价并得出最终的排名。
出题阶段¶
每个队伍需要提出两个Challenge到challenge题库
首先各个受邀参赛队伍都必须在正式比赛前出 2 道Challange。参赛队伍将有 12 周的时间准备Challenge。出Challenge的积分占总分的 30%。
Challenge 1: must be on the Linux platform;
Challenge 2: No platform restriction(except Linux) No challenge type restriction (Pwn, Reverse...)
传统的 BELLUMINAR 赛制要求出的两道Challenge中一道 Challenge 必须是在 Linux 平台,另外一个Challenge则为非 Linux 平台。两个 Challenge 的类型没有做出限制。因此队伍可以尽情展现自己的技术水平。
为使比赛Challenge类型比较均衡,也有采用队伍抽签出Challenge的方式抽取自己的Challenge,这要求队伍能力水平更为全面,因此为了不失平衡性,也会将两道 Challenge 的计入不同分值(比如要求其中一道 Challenge 分值为 200,而另外一道分值则为 100)。
提交部署¶
题目提交截止之前,各个队伍需要提交完整的文档以及解题 Writeup,文档中要求详细标明题目分值,题面,出题负责人,考察知识点列表以及题目源码。而解题 Writeup中则需要包含操作环境,完整解题过程以及解题代码。
题目提交之后主办方会对题目和解题代码进行测试,如果期间出现问题则需要该题负责人配合以解决问题。最终放到比赛平台上。
解题竞技¶
进入比赛后,各支队伍可以看到所有其他团队出的题目并发起挑战,但是不能解答本队出的题目,不设 First Blood 奖励,根据解题积分进行排名。解题积分占总分的 60%。
分享讨论¶
比赛结束后,队伍休息,并准备制作分享 PPT(也可以在出题阶段准备好)。分享会时,各队派 2 名队员上台分享出题解题思路,学习过程以及考察知识点等。在演示结束后进入互动讨论环节,解说代表需要回答评委和其他选手提出的问题。解说没有太多的时间限制,但是时间用量是评分的一个标准。
计分规则¶
出题积分(占总分 30%)有 50% 由评委根据题目提交的详细程度,完整度,提交时间等进评分,另外 50% 则根据比赛结束后的最终解题情况进行评分。计分公式示例: Score = MaxScore -- | N -- Expect_N | 。N代表解出该题的队伍数量,而 Expect_N 则是这道题预期解出的题目数量。只有当题目难度适中,解题队伍数量越接近预期数量 Expect_N,则这道题的出题队伍得到的出题积分越高。
解题积分(占总积分 60%)在计算时不考虑 First Blood 奖励。
分享积分(占 10%)由评委和其他队伍根据其技术分享内容进行评分得出(考虑分享时间以及其他限制),会计算平均值。
赛制总评¶
赛制中将 Challenge 的出题方交由受邀战队,让战队能尽自己所能互相出题,比赛难度和范围不会被主办方水平限制,同时也能提高 Challenge 的质量,每个战队都能有不一样的体验与提升。在"分享"环节,对本队题目进行讲解的同时也在提高自己的能力水平,在讨论回答的过程更是一种思维互动的环节。可以在赛后的学习总结中能得到更好的认知。
攻防模式 - Attack & Defense¶
概述¶
攻防模式常见于线下决赛。在攻防模式中,初始时刻,所有参赛队伍拥有相同的系统环境(包含若干服务,可能位于不同的机器上),常称为 gamebox,参赛队伍挖掘网络服务漏洞并攻击对手服务获取 flag 来得分,修补自身服务漏洞进行防御从而防止扣分(一般来说防御只能避免丢分,当然有的比赛在防御上可以得分)。
攻防模式可以实时通过得分反映出比赛情况,最终也以得分直接分出胜负,是一种竞争激烈,具有很强观赏性和高度透明性的网络安全赛制。在这种赛制中,不仅仅是比参赛队员的智力和技术,也比体力(因为比赛一般都会持续 48 小时),同时也比团队之间的分工配合与合作。
一般比赛的具体环境会在开赛前一天或者当天开赛前半小时由比赛主办方给出(是一份几页的小文档)。在这一段时间内,你需要根据主办方提供的文档熟悉环境并做好防御。
在比赛开始前半小时,这半小时内是无法进行攻击的,各支队伍都会加紧熟悉比赛网络环境,并做好防御准备。至于敌方 Gamebox 的 IP 地址,则需要靠你自己在给出网段中发现。
如果是分为上午下午两场攻防赛的话,那么上午和下午的 Gamebox 漏洞服务会更换(避免比赛中途休息时选手交流),但管理时要用的 IP 地址什么的不会改变。也就是 下午会换新题 。
一般情况下,主办方会提供网线,但并不会提供网线转接口,所以需要自备。
基本规则¶
攻防模式一般的规则如下
- 战队初始分数均为 x 分
- 比赛以 5/10 分钟为一个回合,每回合主办方会更新已放出服务的 Flag
- 每回合内,一个战队的一个服务被渗透攻击成功(被拿 Flag 并提交),则扣除一定分数,攻击成功的战队平分这些分数。
- 每回合内,如果战队能够维护自己的服务正常运行,则分数不会减少(如果防御成功加分则会加分);
- 如果一个服务宕机或异常无法通过测试,则可能会扣分,服务正常的战队平分这些分。往往服务异常会扣除较多的分数。
- 如果该回合内所有战队的服务都异常,则认为是不可抗拒因素造成,分数都不减少。
- 每回合内,服务异常和被拿 Flag 可以同时发生,即战队在一个回合内单个服务可能会扣除两者叠加的分数。
- 禁止队伍使用通用防御方法
- 请参赛队伍在比赛开始时对所有服务进行备份,若因自身原因导致服务永久损坏或丢失,无法恢复,主办方不提供重置服务
- 禁止对赛题以外的比赛平台发起攻击,包括但不限于在 gamebox 提权 root、利用主办方平台漏洞等,违规者立刻被取消参赛资格
- 参赛队伍如果发现其他队伍存在违规行为,请立刻举报,我们会严格审核并作出相应判罚。
网络环境¶
文档上一般都会有比赛环境的 网络拓扑图 (如下图),每支队伍会维护若干的 Gamebox(己方服务器) ,Gamebox 上部署有存在漏洞的服务。
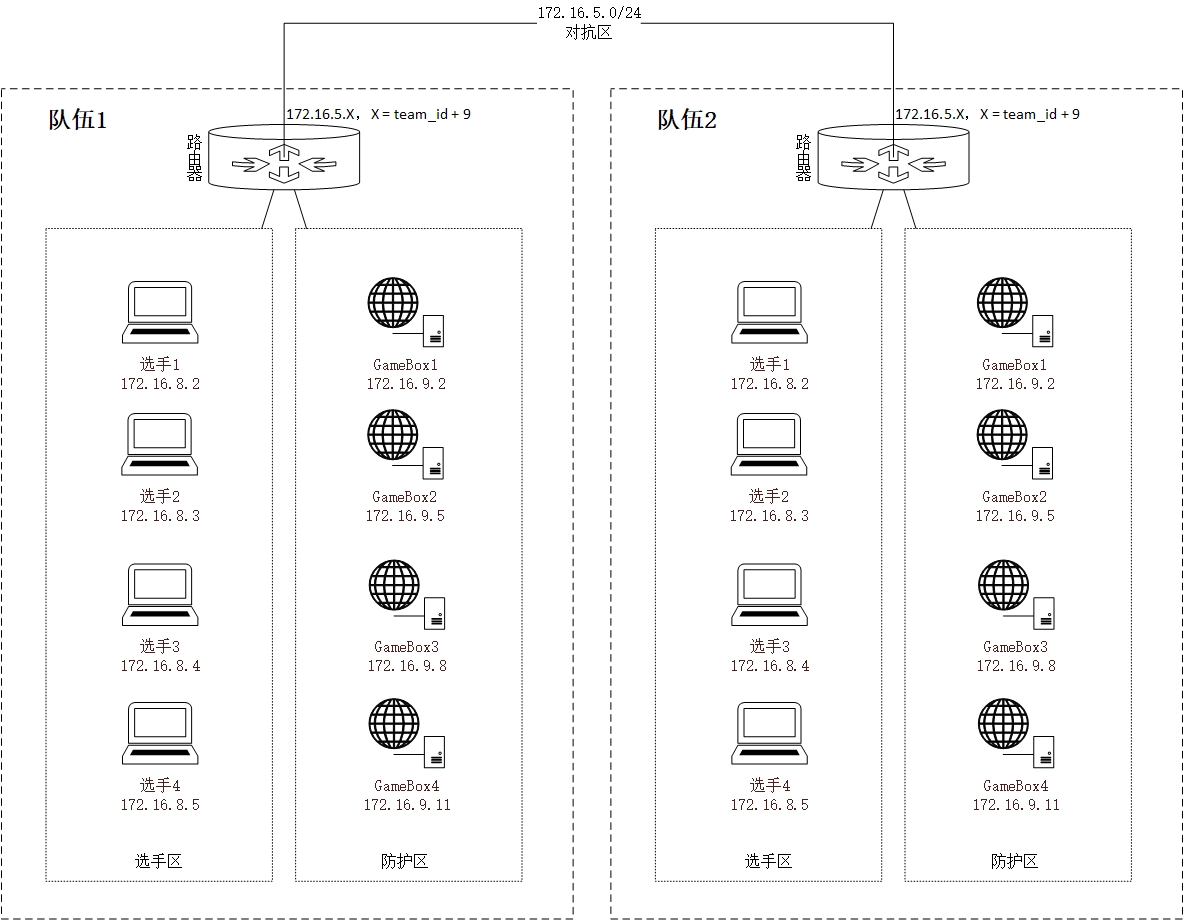
文档上会包括选手,攻防环境,主办方三者的环境。
选手需要在个人电脑上配置或者 DHCP 自动获取
- IP 地址
- 网关
- 掩码DNS 服务器地址
攻防环境
- Gamebox 所处地址,包括己方和其他队伍的地址。
- 比赛一般会提供队伍的 id 与对应 ip 的映射表,以便于让选手指定恰当的攻防策略。
主办方环境
- 比赛答题平台
- 提交 flag 接口
- 流量访问接口
访问 Gamebox¶
参赛文档中会给出队伍登录 gamebox 的方式,一般来说如下
- 用户名为 ctf
- 一般会通过 ssh 登录,登录方式为密码或者私钥。
自然,在登录上战队机器后应该修改所有的默认密码,同时不应该设置弱密码。